Network Security Policy Example
Microsoft cloud products and services and community safety. 01/03/2017; 37 mins to learn Members. On this article. Microsoft cloud products and services ship hyper-scale products and services and infrastructure, enterprise-grade functions, and lots of alternatives for hybrid connectivity. On this bankruptcy, you learn to increase a complete community safety coverage to counter threats towards knowledge safety. In a UUCP community, customers are recognized within the structure host!userid.The “!” persona (pronounced “bang” in networking circles) is used to split hosts and customers. Educational: 802.1X Authentication by the use of WiFi – Lively Listing + Community Coverage Server + Cisco WLAN + Staff Coverage Unfastened knowledge safety coverage templates courtesy of the SANS Institute, Michele D. Guel, and different knowledge safety leaders. This text supplies fundamental explanations about core community safety ideas and necessities, and data on what Azure gives in every of those spaces. .
The previous mantra of “agree with however test” simply isn’t operating. “By no means agree with and test” is how we should observe safety on this technology of subtle breaches. Having a look at 2014 within the rear-view replicate there was a myriad of safety breaches. Goal’s breach uncovered over 40 million bank card Transport large COSCO brutalized through ransomware assault. A still-unknown form of ransomware has led to main issues for COSCO, one of the most United States’ most sensible delivery corporations. Community Safety Auditing (Cisco Press Networking Generation Collection) [Chris Jackson] on Amazon.com. *FREE* delivery on qualifying gives. This entire new information to auditing community safety is an indispensable useful resource for safety */ This word list comprises an inventory of phrases, abbreviations, and acronyms ceaselessly used when discussing networks, safety, firewalls, and WatchGuard merchandise. .
Community Safety Coverage (Code of ethics) Mr. Stevenson´s ITGS
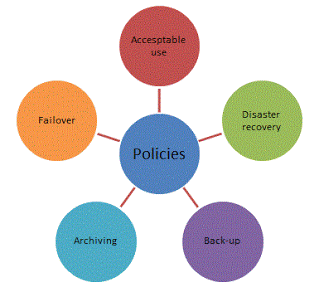
Via : websites.google.com
community safety coverage instance

Via : www.frugalhomebrewer.com
Pattern Cloud Utility Safety and Operations Coverage [release]
![Sample Cloud Application Security and Operations Policy [release] Sample Cloud Application Security and Operations Policy [release]](https://emmamcintyrephotography.com/wp-content/uploads/2018/08/network-security-policy-example-sample-cloud-application-security-and-operations-policy-release-16-638.jpg)
Via : www.slideshare.web
community safety coverage instance

Via : www.frugalhomebrewer.com
Safety Insurance policies and Procedures ppt obtain

Via : slideplayer.com
community safety coverage instance
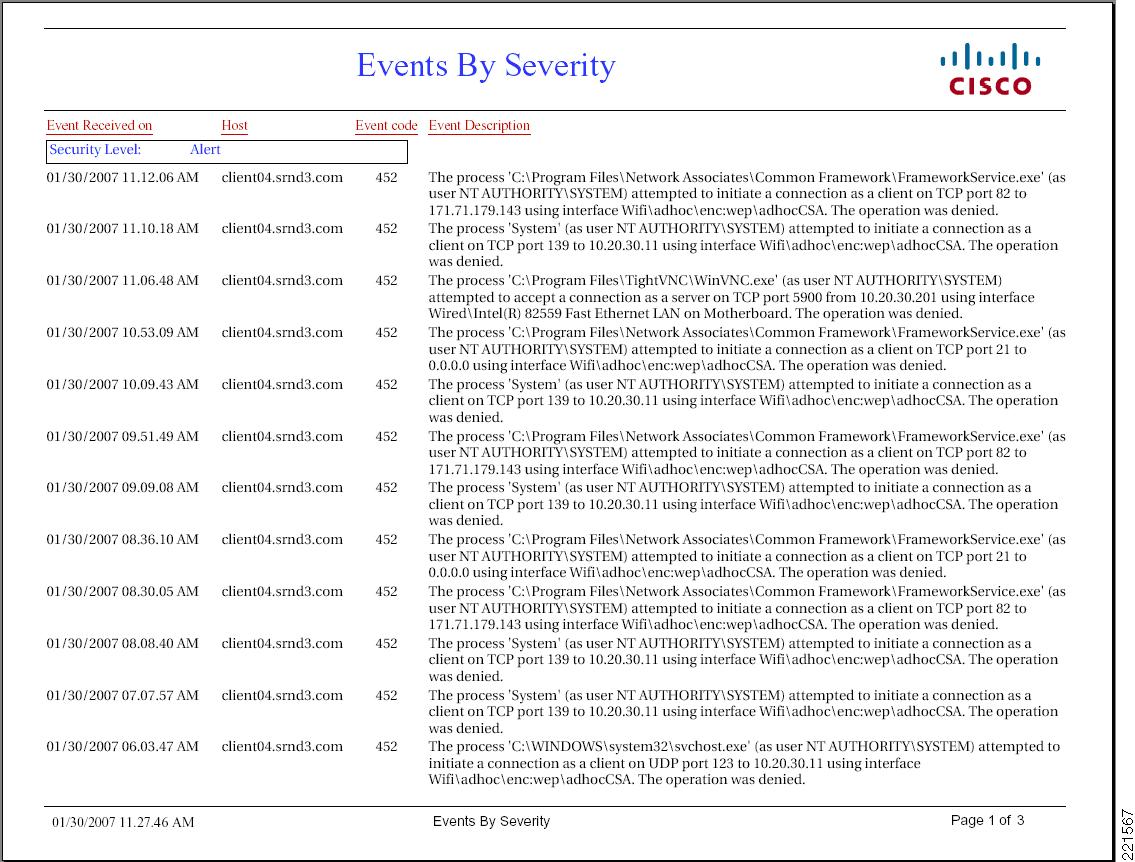
Via : www.frugalhomebrewer.com
Wi-fi and Community Safety Integration Answer Design Information

Via : www.cisco.com
community safety coverage instance
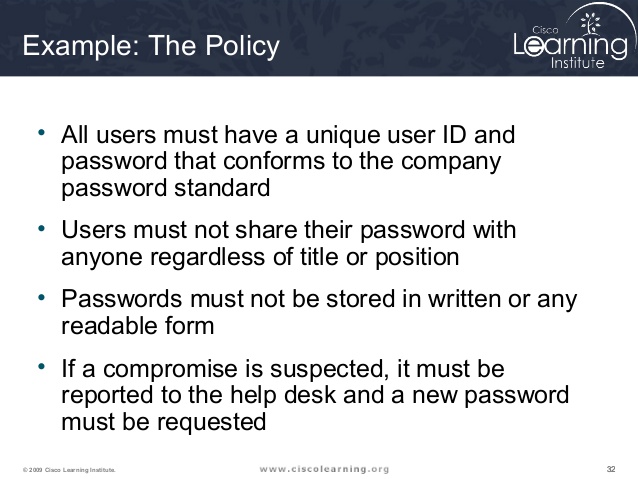
Via : 1cashing.information
If you do not have a valid policy, we recommend that you develop one before implementing your digital environment. The policy consists of at least one that we call CSP directives. Developing a comprehensive data security policy for your company can be a tedious job, but it is one of the most important things you can do to help your organization and your clients, we do not need to remind you how serious a violation can be.
Reports are crucial and should be enabled because they allow you to see the CSP failures reported by browsers, as they interact with your website. For example, a part of the report could examine the attribute of its security controls. The policy reports are a means to find the conditions you prefer to find in your cumulative security policy of Dome9.
As the owner of a site, it is recommended to take into account the security problems that may affect your website. The simple fact of the problem is that the bad guys are always waiting to catch us. One of the most important facts regarding web development is security. A very simple example could be a password protection policy. Example The following is an instance to generate an RSA key pair.
Observe the way namespaces are labeled, which is necessary for network policies. Network policies are easy to implement and can be implemented in the same way despite the characteristics of the application. At this point, you have a newly configured network policy that you can use to identify who accesses your network and with what type of machine. Network policies provide you with a way to declaratively configure which pods are allowed to connect with each other. If a policy does not meet the needs of the business, it will not make sense because the IT service provider has as its fundamental objective to provide services and processes for the use of the organization. Performance management policies can allow you to identify underutilized and underutilized infrastructures in your environment.
Security is not a game of one person. Security is a component of intention. Cyber ??security is everyone’s responsibility. Information security is integral to the management of your organization and to ensuring that vital information is not compromised in any way. A security policy is a formal plan that addresses how security will be implemented in an organization. What follows is that it does not pretend to be a step-by-step break from everything you need to create perfect data security, it’s a summary of the great hitters that come together to create an excellent basis for data security.
Networks can be private, such as, for example, a network within a company or public. For example, your network may have to be inactive for more than 8 hours before business interruption coverage is applied. Wireless networks are more prone to interception than wired networks.
Without this type of approach, the business runs the risk of overspending in some regions and neglecting others, leaving weaker links that can lead to security incidents as infractions. When you learn that the security of your institution was compromised, the previous thing you want to do is to panic. Obviously, providers rarely tell you exactly what they do not do. Even when you have to change providers in the cloud to find the security you need, it’s worth the investment. Your information backup assistance, for example, should have the ability to encrypt that data for you.
CCNA Safety 02 basics of community safety

Via : www.slideshare.web
community safety coverage instance

Via : architecture-nice.com
CCNA Safety 02 basics of community safety

Via : www.slideshare.web
community safety coverage instance

Via : architecture-nice.com
Safety Coverage Template 7 Unfastened Phrase, PDF Report Downloads

Via : www.template.web
community safety coverage instance

Via : slideplayer.com
Beautiful Data Safety Coverage Doent Template Photographs Gallery

Via : kiwidesigns.us
community safety coverage instance
![Sample Cloud Application Security and Operations Policy [release] Sample Cloud Application Security and Operations Policy [release]](https://emmamcintyrephotography.com/wp-content/uploads/2018/08/network-security-policy-example-network-security-policy-template-information-security-policy-template-sample-9-documents-within.jpg)
Via : www.slideshare.web
Safety Insurance policies And Procedures Template Pccc.us

Via : www.pccc.us
community safety coverage instance

Via : slideplayer.com
community safety coverage template knowledge safety coverage

Via : www.frugalhomebrewer.com
community safety coverage instance
![Sample Cloud Application Security and Operations Policy [release] Sample Cloud Application Security and Operations Policy [release]](https://emmamcintyrephotography.com/wp-content/uploads/2018/08/network-security-policy-example-sample-cloud-application-security-and-operations-policy-release-23-638.jpg)
Via : www.slideshare.web
Similar Posts:
- Security Incident Response Plan Template
- Social Media Strategy Examples
- Certificate Of Insurance Template
- Disaster Recovery Plan Sample
- Business Card With Social Media
- Business Cards With Social Media
- Shipping Label Example
- Service Contract Agreement
- Service Contract Template Doc
- Membership Application Template
- Marketing Report Example
- Sales Receipt Form
- Cleaning Bid Sheet
- Facebook Business Page Design
- Social Media Business Card
- Theatre Resume Example
- Web Site Launch Press Release
- Business Cards Social Media
- Corporate Brochure Design
- Contractor Invoice Template Excel
- New Hire Press Release
- Social Media Reporting Templates
- Basic Non Disclosure Agreement
- Simple Consulting Agreement Template
- Social Media Report Template
- Electrical Engineering Student Resume
- Disaster Recovery Plan Example
- Pricing Sheet Template
- Deposit Receipt Template
- Strategic Business Plan Example
- Inventory Management In Excel Free Download
- Provisional Patent Application Example
- Mutual Nda Template
- Social Media On Business Cards
- Corporate Business Cards
- Sample Letters Asking For Donations
- Event Flyer Templates Free
- General Contractor Contract
- Inventory Tracking Sheet
- Hipaa Fax Cover Sheet
- Financial Advisor Business Plan
- Circuit Breaker Directory Template
- Lawn Service Proposal Template Free
- Sample Letter Asking For Donation
- Quickbooks Pay Stub Template
- Web Hosting Templates
- Confidentiality Agreement Form
- Sample Employee Recognition Programs
- Simple Equipment Rental Agreement Template Free
- Facebook Business Page Template
- Branding Strategy Template
- Sample Signup Sheet
- Nutrition Labels Template
- New Product Press Release
- Social Media Web Templates
- Personal Trainer Business Plan
- Demographic Questionnaire Pdf
- Itemized Receipt Template
- Snow Removal Contracts Templates
- Stock Pitch Template
- Job Bid Template
- Free Newsletter Template
- Night Club Flyer
- Nanny Resume Template
- Half Fold Brochure Template
- Snow Removal Contract Templates
- 30 60 90 Sales Plan
- Non Compete Agreement Form
- Corporate Business Card
- Income Statement Template Excel
- Free Invoice Template Google Docs
- Printable Inventory Template
- Deposit Receipts Template
- Accounting T Charts
- Sample Offer Letter
